The International Maritime Organization (IMO) has developed many international conventions to protect the safety of the crew, cargo, and the environment. Nonetheless maritime accidents still happen resulting in losses of lives, property, and damage to the marine environment.
The main reasons for these accidents include:
- human error,
- ageing ships,
- improper maintenance on board ships to reduce costs,
- increasing lack of experienced crew due to shortage of trained manpower and non-compliance with minimum international safety standard.
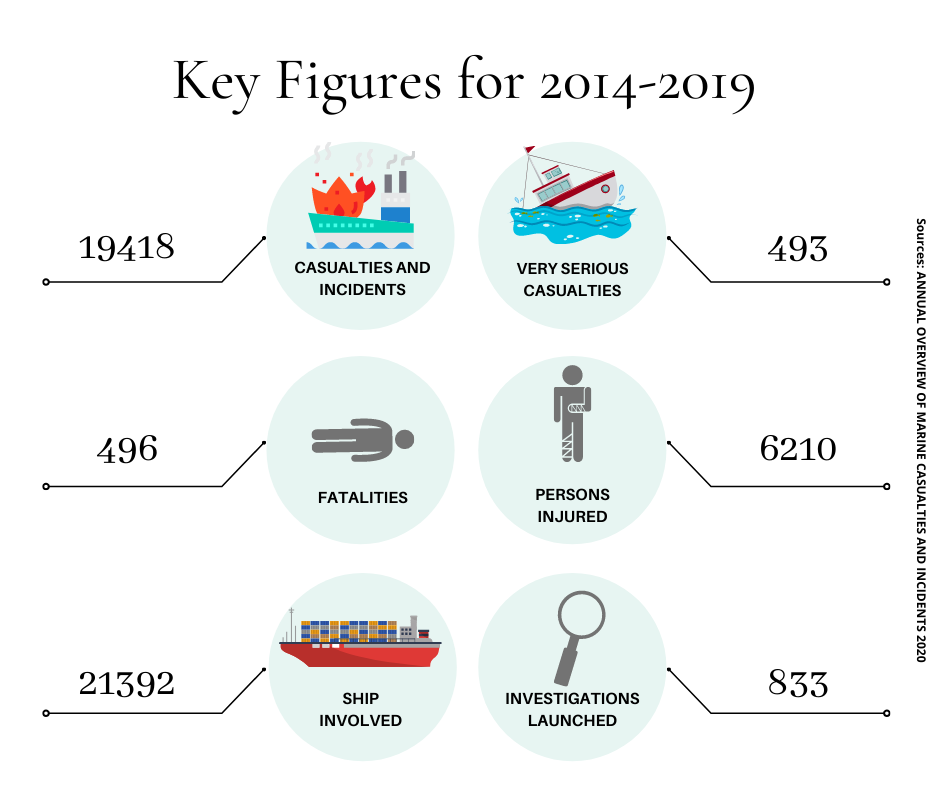
According to the European Maritime Safety Administration’s Annual Overview of Maritime Casualties and Incidents 2020 report: The total number of reported marine casualties and incidents over the period 2014-2019 is 19418. These incidents led to 493 very serious casualties, 496 fatalities and 6210 persons injured. This data combined with decades of maritime related serious environmental disasters, latest being the Oil spill from Crimson Polaris that had about 1,550 metric tonnes of heavy oil and about 130 metric tonnes of diesel oil on board.
Despite strict controls by classification societies, flag states, port state controls, insurers and brokers, inferior ships continue to operate and pose serious risks to human life and the environment. This is illustrated by the ship detention records recorded annually in the annual reports of all MOUs and the U.S. Coast Guard. Port state control is not a substitute for effective flag state control and by itself it is unlikely that inferior ships will be eliminated. The existence of inferior ships calls into question the way in which the condition of ships is checked, recorded and shared among stakeholders by port and flag states.
In this blog we focus on the critical role of ship inspection and data sharing in improving safety and environmental protection at sea. Various Inspection like, Annual Flag State Safety Inspection, Port State Control (PSC) Inspections, Classification Society Routine Inspections, Owners/ Charterers/ Insurance Vessel Condition Inspection, have been the primary mode to ascertain condition of vessel and the data collected forms the basis of many important decisions within the industry which has serious implication for Safety of life at Sea and the Maritime Environment.
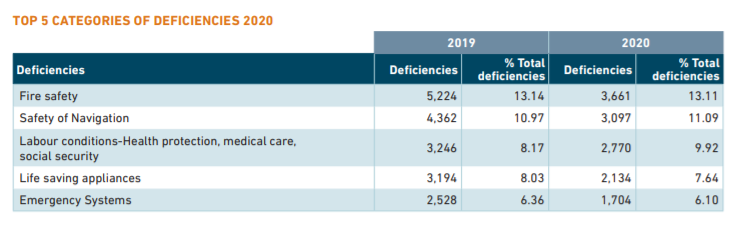
Investigation reports into various Maritime Accidents as compiled on IMO GISIS points to human error – related to quality control and inspections – as one of the leading contributing factors. The below table shows the leading factors for ship deficiency as recorded under Paris MOU annual report for the year 2020.
Fire Safety and Safety of Navigation being the top categories of deficiencies underscores the importance of precise recording, reporting, data access for reference and follow up across jurisdictions to avoid impending loss of life and potential marine pollution. This record of deficiencies together with the recurring nature of maritime accidents begs for a deeper analysis and understanding of the tools, methods and process in place.
Common pain points of a Manual Technical Survey include:
- Loss of life and irreparable environmental damage due to the manual surveying and control methods used in the shipping industry for centuries.
- On an average it takes up to seven days of planning, liaison with various parties and physical survey for each vessel to produces PDF reports like the ones below that usually sits dormant in PDF files.
- Historical data on ship conditions and defects are incomprehensible (static PDF reports). The lack of precise data often leads to incorrectly calculated political decisions. One such example is the PSC inspection report for all MOUs in PDF format with little or no follow-up to the deficiencies found. As soon as a ship is allowed to sail after a warning and recommendation from a PSC officer, the written text in PDF files is seldom detailed in the existing online data exchange systems (e.g., Equasis and Paris MOU detention list) which provides a brief on the vessel detention.
- In addition, much of the critical ship inspection information is lost due to its non-digital nature which inherits easy sharing and is prone to misunderstanding when read by other participating port state administrations. This practice sometimes results in substandard ships failing to meet regulatory requirements.
There are several important factors that deserve attention and improvement; We need a solution to address the problem of human error and data loss and to improve the currently mostly manual format of inspection and PDF-based reporting that is practiced in the maritime industry.
Cyber Smart – The Solution!
Solving this problem of dangerous oversight, human error and data loss in the shipping industry through Cyber Smart – a web and mobile-based e-survey platform that ensures that inspection authorities are equipped with a digital survey tool that enables them to digitally transmit the survey data an app.
Cyber Smart – A Web and Mobile Application for Survey Planning, Conduct of Survey, Survey Report Generation. It is an advanced format agnostic SaaS platform taking data collection and analysis to the next level. It leverages the most advanced cloud computing infrastructure running our proprietary algorithm to spin out trends, using both collected and historical data.
We use our proprietary algorithm and the most advanced cloud computing infrastructure to generate trends from collected and historical data. The platform is revolutionizing the way inspections are performed in the shipping industry and has the potential to revolutionize data collection and analysis across industries. This mobile application is more suitable for Surveyors as there are no physical documents involved to delay the process.
Why choose Cyber Smart?
- Ground Surveyor uses mobile app to collect data while onboard the ship, our mobile application allows users to achieve the highest degree of digital visualization and offers the capability of collecting all types of data.
- One click report generation in any format. Time and effort saved.
- More time to focus on the critical check items that matter, thus reducing the human error that contributes to 58% of Marine incidents.
- Consolidation of crucial data sets through smart analytics to inform sectoral policy formulation
- Better protection of Marine environment and life at sea through advanced pre-emptive maintenance of vessel thus avoiding shipping related environmental disasters.
Features of Cyber Smart:
- The Web based version of CyberSmart positions the users to access survey data, monitor deficiency trends through customised data analytics and to extract key reports in all required format – this feature allows for seamless integration with the present system in place. CyberSmart takes away the human error element in recording of key survey data and can generate customised reports through a mouse-click.
- Our Mobile app allow surveyors to conduct digital inspections, and one of the key features of the application is that the mobile app communicates with web application
- Digital Survey Management reduces manhour spent in planning, allocation, conduct and report generation.
- Vessel tracking and survey allocation to ground surveyor using online dashboard
- Various report formats are generated digitally once all data is synced to the cloud server
- Secure Data Repository feeds into AI driven key visualization displayed on user interface
Still want to know more about Cyber Smart. Request a demo at: tech@cyberwaves.eu
Authors
Deepthi Bennan & Richa Dutt Nandan
Marketing Managers,
Cyberwaves B.V. & Varuna Marine B.V